That One Password You Love Is Probably Ruining Your Digital Life
Let’s be honest. Most people have a favorite password. It is familiar, easy to type, and feels safe because it has “worked” for years. You drop it into email accounts, apps, streaming services, and maybe even work tools. It feels efficient, like using one key for every door. That convenience, though, comes with a hidden price tag. Hackers love habits. Reused passwords turn one small crack into a full collapse. When one service slips, everything connected to that password becomes fair game. It is not dramatic paranoia. It is basic digital physics. One fall knocks over every domino.
One Leak Can Open Every Door
Data breaches happen constantly, often without headlines. A shopping app or an old forum gets compromised, and login details are spilled quietly. Hackers then try those same credentials everywhere else. Email, cloud storage, social media. The chain reaction is fast. See, people assume attacks are personal. But, they rarely are. Automated scripts do the work while you sleep. That reused password turns into a master key. Suddenly, your accounts are no longer separate spaces. They become rooms without walls. The scary part is the delay. Damage may appear weeks later. By then, the trail is cold and frustrating. One reused password creates cleanup work nobody enjoys.
Your Email Is the Crown Jewel
Email accounts sit at the center of digital life. Password resets, alerts, and confirmations all land there. If someone gains access, they can quietly reset everything else. Banking apps, subscriptions, work platforms. It cascades fast. Many people protect their email with the same password used elsewhere. That is like locking your house but leaving the key under the mat. Once email access is gained, the rest becomes a checklist. Hackers do not rush. They wait and observe. This is why email security matters more than most apps. Treat it like a vault, not a convenience login. One strong barrier here can limit massive fallout.
Memory Is a Terrible Security System
Brains are amazing, but they are not password managers. People reuse passwords because remembering dozens feels exhausting. That trade-off feels reasonable until something breaks. Convenience wins short-term, pain follows later. Patterns make things worse. Adding a number or symbol feels clever, but attackers expect it. Passwords created by habit share predictable shapes. That predictability is exactly what automated attacks exploit. Tools exist to carry the mental load. They store, generate, and autofill without effort. Once set up, life gets easier, not harder. Security improves quietly in the background.
Small Accounts Still Matter

It is easy to dismiss “unimportant” accounts. A game login or random newsletter feels harmless. Those accounts still store emails, names, and patterns. Hackers use them as stepping stones. Smaller services often have weaker defenses. That makes them attractive targets. Once compromised, they feed data into larger attacks elsewhere. One tiny breach can snowball into identity headaches. Every login deserves respect. Not panic, just intention. Separating passwords limits how far damage can spread. Containment is powerful.
Changing Habits Without Losing Your Mind
Switching habits sounds exhausting, but it does not need drama. Start with the most sensitive accounts first. Email, banking, and cloud storage come before everything else. Progress beats perfection. Of course, it also means letting technology help you. Password managers generate strong passwords and remember them for you. After setup, logging in becomes faster, not slower. Autofill feels like cheating in the best way. Security is not about fear. It is about reducing risk with smart defaults. One password everywhere used to feel clever. Today, it is outdated. Your future self will appreciate the upgrade.…






















 This classic piece of equipment has been a staple in the industry for decades, capturing some of the most memorable moments in cinematic history. With its impressive image quality and versatility, it’s no wonder that filmmakers continue to choose this tried-and-true workhorse. The 35mm film camera works by exposing photographic film to light through a series of intricate mechanisms. As each frame is exposed, it creates a tangible physical negative that can be developed and edited. This analog process delivers a unique aesthetic charm that digital cameras often struggle to replicate.
This classic piece of equipment has been a staple in the industry for decades, capturing some of the most memorable moments in cinematic history. With its impressive image quality and versatility, it’s no wonder that filmmakers continue to choose this tried-and-true workhorse. The 35mm film camera works by exposing photographic film to light through a series of intricate mechanisms. As each frame is exposed, it creates a tangible physical negative that can be developed and edited. This analog process delivers a unique aesthetic charm that digital cameras often struggle to replicate. These state-of-the-art devices basically make use of cutting-edge technology to deliver high-resolution images with incredible clarity and detail. Thanks to their ability to shoot in various formats, such as RAW or ProRes, they allow for greater flexibility during post-production. Filmmakers can manipulate the footage to achieve their desired look and feel, whether it’s adding special effects or adjusting color grading. Moreover, these cameras offer exceptional low-light performance, ensuring that even dimly lit scenes are captured without compromising quality. This feature greatly enhances a cinematographer’s creativity by expanding shooting possibilities in challenging environments. Additionally, digital cinema cameras often come equipped with advanced features like built-in image stabilization and high-speed frame rates.
These state-of-the-art devices basically make use of cutting-edge technology to deliver high-resolution images with incredible clarity and detail. Thanks to their ability to shoot in various formats, such as RAW or ProRes, they allow for greater flexibility during post-production. Filmmakers can manipulate the footage to achieve their desired look and feel, whether it’s adding special effects or adjusting color grading. Moreover, these cameras offer exceptional low-light performance, ensuring that even dimly lit scenes are captured without compromising quality. This feature greatly enhances a cinematographer’s creativity by expanding shooting possibilities in challenging environments. Additionally, digital cinema cameras often come equipped with advanced features like built-in image stabilization and high-speed frame rates. These compact and maneuverable devices allow cinematographers to achieve angles and perspectives that were once only possible with expensive helicopter rigs or cranes. One of the key advantages of using drone cameras is their ability to fly at different altitudes, providing a unique bird’s-eye view of a scene. This opens up endless creative possibilities for filmmakers to showcase sweeping landscapes or create dynamic chase sequences. With advancements in technology, drone cameras now offer high-resolution image quality, allowing for crystal-clear footage even when capturing fast-paced action scenes. They are equipped with stabilizing features that help eliminate shaky footage, ensuring smooth and professional-looking shots.
These compact and maneuverable devices allow cinematographers to achieve angles and perspectives that were once only possible with expensive helicopter rigs or cranes. One of the key advantages of using drone cameras is their ability to fly at different altitudes, providing a unique bird’s-eye view of a scene. This opens up endless creative possibilities for filmmakers to showcase sweeping landscapes or create dynamic chase sequences. With advancements in technology, drone cameras now offer high-resolution image quality, allowing for crystal-clear footage even when capturing fast-paced action scenes. They are equipped with stabilizing features that help eliminate shaky footage, ensuring smooth and professional-looking shots.
 Businesses need to be able to manage data to make informed decisions and stay competitive effectively. Investing in a good customer relationship management (CRM) system can help you keep track of customer information, sales history, and other important data points. You’ll also want to look into software for managing finances and inventory.
Businesses need to be able to manage data to make informed decisions and stay competitive effectively. Investing in a good customer relationship management (CRM) system can help you keep track of customer information, sales history, and other important data points. You’ll also want to look into software for managing finances and inventory.
 Having mobile access to your data is becoming increasingly crucial for businesses in today’s world. Investing in an excellent mobile platform will allow you to access and work on files anytime. It can improve collaboration and productivity and give customers easy access to your products and services.
Having mobile access to your data is becoming increasingly crucial for businesses in today’s world. Investing in an excellent mobile platform will allow you to access and work on files anytime. It can improve collaboration and productivity and give customers easy access to your products and services.

 Another great way to get more Spotify streams is to submit your playlist to music curators. These people manage Spotify playlists and can feature your music if they think it’s a good fit. You can find a list of curators on websites like Playlist Push. Once you’ve found some potential curators, reach out to them and see if they’re interested in featuring your music.
Another great way to get more Spotify streams is to submit your playlist to music curators. These people manage Spotify playlists and can feature your music if they think it’s a good fit. You can find a list of curators on websites like Playlist Push. Once you’ve found some potential curators, reach out to them and see if they’re interested in featuring your music.
 One of the biggest mistakes businesses make when creating an app is focusing too much on features rather than the user experience. It’s important to remember that people use apps because they’re convenient and easy to use. If your app is difficult to navigate or isn’t intuitive, people will quickly get frustrated and stop using it.
One of the biggest mistakes businesses make when creating an app is focusing too much on features rather than the user experience. It’s important to remember that people use apps because they’re convenient and easy to use. If your app is difficult to navigate or isn’t intuitive, people will quickly get frustrated and stop using it.
 The first and most obvious benefit of using node as a Service is that it allows you to manage your blockchain efficiently and effectively. If you’re running a node yourself, you’ll need to keep up with the latest software updates, monitor the performance of your node, and ensure that it remains online and accessible. It can be time-consuming and difficult, especially if you’re not a technical expert.
The first and most obvious benefit of using node as a Service is that it allows you to manage your blockchain efficiently and effectively. If you’re running a node yourself, you’ll need to keep up with the latest software updates, monitor the performance of your node, and ensure that it remains online and accessible. It can be time-consuming and difficult, especially if you’re not a technical expert. A Node is a Service provider that can pre-configure superficial nodes across many chains and networks. You don’t need to worry about setting up and configuring your nodes yourself. All you need to do is provide the required information and funds, and the node will be set up and maintained by the service provider.
A Node is a Service provider that can pre-configure superficial nodes across many chains and networks. You don’t need to worry about setting up and configuring your nodes yourself. All you need to do is provide the required information and funds, and the node will be set up and maintained by the service provider.
 A spy app is a smartphone application that can be used to monitor another person’s mobile phone activity. This includes text messages, emails, calls, and anything else sent using the device. There are many reasons why someone might want to use a spy app on their child or spouse. They could be worried about their child being bullied at school or if their spouse is cheating on them. To use these apps, install the app from Google Play Store and follow its instructions to access your logs.
A spy app is a smartphone application that can be used to monitor another person’s mobile phone activity. This includes text messages, emails, calls, and anything else sent using the device. There are many reasons why someone might want to use a spy app on their child or spouse. They could be worried about their child being bullied at school or if their spouse is cheating on them. To use these apps, install the app from Google Play Store and follow its instructions to access your logs. WhatsApp logs are files that contain information about your conversations, such as the time and date of each message. You can use these logs to spy on someone’s WhatsApp messages because they provide a way to see all of their activity in one place. The easiest way to access is by using an app like WhatsDog or Monitor for WhatsApp. Both apps are free and work on Android devices. They allow you to download a copy of your WhatsApp conversations and view them in an easy-to-read format.
WhatsApp logs are files that contain information about your conversations, such as the time and date of each message. You can use these logs to spy on someone’s WhatsApp messages because they provide a way to see all of their activity in one place. The easiest way to access is by using an app like WhatsDog or Monitor for WhatsApp. Both apps are free and work on Android devices. They allow you to download a copy of your WhatsApp conversations and view them in an easy-to-read format.
 One of the essential features of a VPN is its strong encryption. It means that your data will be securely encrypted, making it difficult for anyone to spy on or track your activities. A reliable VPN provider will have robust security features, including military-grade encryption. It will also have a strict no-logs policy, meaning that your data will never be stored or tracked.
One of the essential features of a VPN is its strong encryption. It means that your data will be securely encrypted, making it difficult for anyone to spy on or track your activities. A reliable VPN provider will have robust security features, including military-grade encryption. It will also have a strict no-logs policy, meaning that your data will never be stored or tracked. Another essential factor in a reliable VPN provider is the privacy policy. A good VPN should have an airtight privacy policy so that your data remains secure and private while you are using their servers. Furthermore, since no one can see what sites or services you visit, it also means that even your ISP won’t track your activities.
Another essential factor in a reliable VPN provider is the privacy policy. A good VPN should have an airtight privacy policy so that your data remains secure and private while you are using their servers. Furthermore, since no one can see what sites or services you visit, it also means that even your ISP won’t track your activities.
 Another importance of pay stubs is that they serve as proof of employment. This is especially handy if an employee needs to furnish this document to prove their income for any reason, such as taking out a loan or applying for a loan.
Another importance of pay stubs is that they serve as proof of employment. This is especially handy if an employee needs to furnish this document to prove their income for any reason, such as taking out a loan or applying for a loan. It’s also important to mention that pay stubs are useful for tax preparation purposes. Employees can utilize their past year of paystubs in order to help them with their yearly income taxes, which saves them a considerable amount of time and money since they won’t have to figure all this information out themselves or spend extra cash on hiring an accountant to do it for them.
It’s also important to mention that pay stubs are useful for tax preparation purposes. Employees can utilize their past year of paystubs in order to help them with their yearly income taxes, which saves them a considerable amount of time and money since they won’t have to figure all this information out themselves or spend extra cash on hiring an accountant to do it for them.
 If you are running a small business, you do not have adequate resources to check your systems for security vulnerabilities. Robust firms provide you access to security experts. These experts can discover and fix weak areas in your applications and networks. When choosing an IT support firm, make sure you consider various professional certifications. Also, you should consider experience.
If you are running a small business, you do not have adequate resources to check your systems for security vulnerabilities. Robust firms provide you access to security experts. These experts can discover and fix weak areas in your applications and networks. When choosing an IT support firm, make sure you consider various professional certifications. Also, you should consider experience. The right IT support firm does not allow your tickets to go unanswered. Instead, it should always communicate the status of the open tickets and work to resolve them. There is a need to have a service level agreement. This helps mitigate arising issues because you have documented all the services you need. If your IT support company fails to meet the agreed targets, you should consider switching providers.
The right IT support firm does not allow your tickets to go unanswered. Instead, it should always communicate the status of the open tickets and work to resolve them. There is a need to have a service level agreement. This helps mitigate arising issues because you have documented all the services you need. If your IT support company fails to meet the agreed targets, you should consider switching providers.
 Believe it or not, updates to the different types of software or applications are being released every single day. And, of course, you wouldn’t want your company to be left behind. Instead of spending lots of money and a great deal of your time trying to update your system, why not just leave the job to the experts? The best IT support service provider should be able to manage your company’s tools, software, hardware, and system better than anyone else. They know what’s new, and they will surely keep your business in the loop.
Believe it or not, updates to the different types of software or applications are being released every single day. And, of course, you wouldn’t want your company to be left behind. Instead of spending lots of money and a great deal of your time trying to update your system, why not just leave the job to the experts? The best IT support service provider should be able to manage your company’s tools, software, hardware, and system better than anyone else. They know what’s new, and they will surely keep your business in the loop.




 role in boosting different business processes. It is possible when you incorporate different systems that allow you to run a number of processes smoothly. To make sure your company is up to date with the latest, you should look for an IT service provider.
role in boosting different business processes. It is possible when you incorporate different systems that allow you to run a number of processes smoothly. To make sure your company is up to date with the latest, you should look for an IT service provider. for your company. They will always be ready to assist with the challenges you or your customers are experiencing with certain online services. Look for an IT service provider that is available 24 hours a day to get the kind of support you need.…
for your company. They will always be ready to assist with the challenges you or your customers are experiencing with certain online services. Look for an IT service provider that is available 24 hours a day to get the kind of support you need.…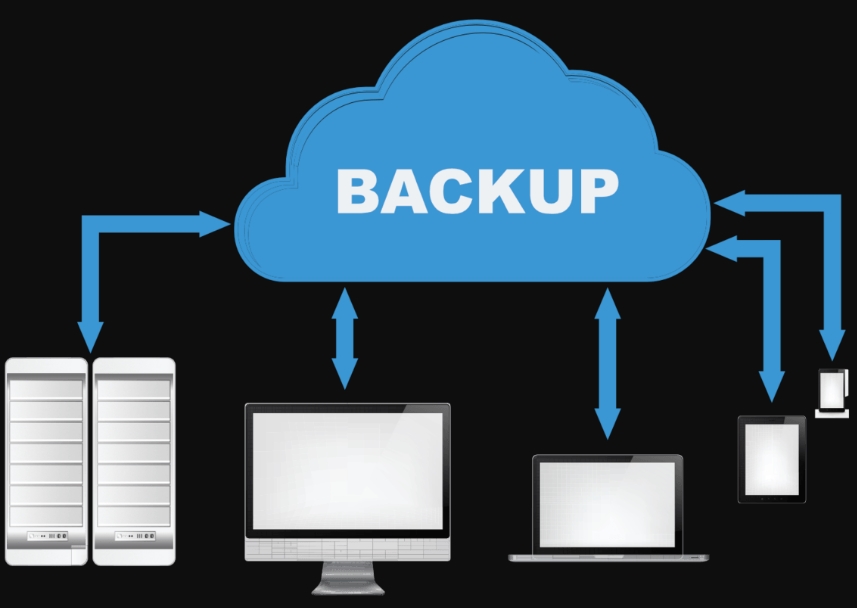
 Slow operating servers and unresponsive datastores could cost you days or weeks of operation. It will, in turn, lead to poor customer service and low productivity.
Slow operating servers and unresponsive datastores could cost you days or weeks of operation. It will, in turn, lead to poor customer service and low productivity.
 recreational or sporting purposes. You should also be prepared for different emergencies involved in this activity. Crashing or falling off is usually common when skiing. Carrying a radio call or going for the activity with a partner is vital for your safety. There are other tech devices you should take to have the best skiing experience. They include:
recreational or sporting purposes. You should also be prepared for different emergencies involved in this activity. Crashing or falling off is usually common when skiing. Carrying a radio call or going for the activity with a partner is vital for your safety. There are other tech devices you should take to have the best skiing experience. They include: will help you capture a lot of things. Most smartwatches help you keep track of your fitness. You will also come across those that have GPS tracking features that help others know your whereabouts as you carry on with the activity. Carry these high-tech devices for the best skiing expedition.…
will help you capture a lot of things. Most smartwatches help you keep track of your fitness. You will also come across those that have GPS tracking features that help others know your whereabouts as you carry on with the activity. Carry these high-tech devices for the best skiing expedition.…
 Ideally, you need to make great tracks. If you are planning to make great music, then you need to start with the right music. Ensure you do your best to make your music as compelling as you can before starting your promotion. Therefore, you should take time to master your music, perfect your music, and produce great tracks. After finishing creating your music, you can confidently promote it online.
Ideally, you need to make great tracks. If you are planning to make great music, then you need to start with the right music. Ensure you do your best to make your music as compelling as you can before starting your promotion. Therefore, you should take time to master your music, perfect your music, and produce great tracks. After finishing creating your music, you can confidently promote it online. As far as building a fanbase is concerned, promoting your music is the ultimate goal. You should connect with people who support your music by attending shows, purchasing your merchandise, and streaming tracks. However, the process of building a fanbase from scratch is quite difficult. You need to use all the tools you have got at your disposal.…
As far as building a fanbase is concerned, promoting your music is the ultimate goal. You should connect with people who support your music by attending shows, purchasing your merchandise, and streaming tracks. However, the process of building a fanbase from scratch is quite difficult. You need to use all the tools you have got at your disposal.… Data loss is one of those tragedies that most computer users have to deal with at some point in their lives. Some incidences of data loss might be simple, but there instances when the magnitude of the loss can hurt you to the core. In light of this fact, this write-up explores some of the common causes of computer data loss and some precautions possible precautions against them.
Data loss is one of those tragedies that most computer users have to deal with at some point in their lives. Some incidences of data loss might be simple, but there instances when the magnitude of the loss can hurt you to the core. In light of this fact, this write-up explores some of the common causes of computer data loss and some precautions possible precautions against them.
 The first step to
The first step to 