Data Management and Backup Through Managed IT Services
Data is the foundation of modern business operations. Every transaction, message, and system process relies on accurate information. Losing data can stop work, damage trust, and create legal risk. Managing data internally is difficult as systems grow more complex. An IT Company in Ottawa providing managed IT services offers structured support for data management and backup. They help businesses protect information, maintain availability, and recover quickly from incidents. This article explains how managed IT services handle data management and backup to support secure and reliable operations.
Understanding the Importance of Data Management
Data management involves organizing, storing, and maintaining information throughout its lifecycle. Businesses generate large volumes of data every day. Without proper control, data becomes fragmented or outdated. Managed IT services create clear data policies. Information is categorized and stored correctly. Access rules are applied consistently. This approach improves accuracy and usability. A unique benefit is having expert oversight that keeps data structured and aligned with business needs.
Scheduling and Automated Backup Strategies

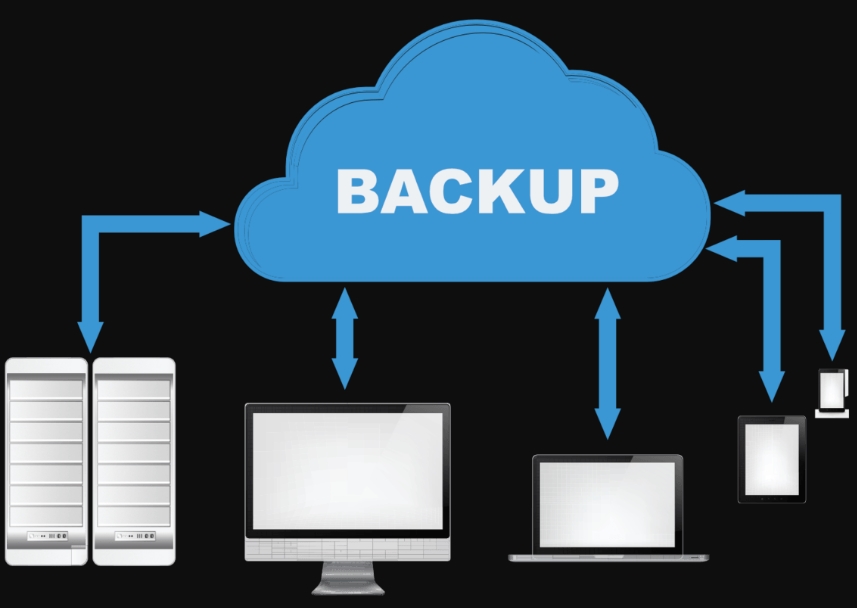
Reliable backups protect against unexpected loss. Managed IT services implement automated backup schedules. Data is backed up regularly without manual effort. Backups may occur daily or more often based on importance. Automation reduces human error. It also ensures consistency. Backup processes are monitored to confirm completion. This approach helps ensure critical data is always protected and ready for recovery when needed.
Centralizing Storage and System Organization
Centralized storage simplifies data access and control. Managed IT providers design systems where data resides in secure, unified environments. This reduces duplication and confusion. Files are easier to locate and manage. Centralization also supports better monitoring. Storage performance can be optimized continuously. With clear organization, teams work more efficiently. Central systems also make it easier to apply security and backup rules across all data assets.
Securing Backup Storage and Encryption
Backup data must remain secure. Managed IT services use encrypted storage solutions. Encryption protects data during transfer and while at rest. Backups may be stored offsite or in secure cloud environments. This separation protects against physical damage or local system failure. Access to backup data is restricted. Security controls reduce the risk of unauthorized use or data leaks.
Restoring and Fast Data Recovery
Backups only matter if recovery works. Managed IT services test restoration processes regularly. This confirms that data can be recovered quickly and accurately. During incidents, recovery follows a clear sequence. Systems are restored without unnecessary delay. Downtime is reduced. Employees regain access to information faster. Efficient recovery supports business continuity and customer confidence during disruptions.
Monitoring Data Health and Performance

Ongoing monitoring keeps data systems healthy. Managed IT providers track storage capacity and performance. Issues like slow access or failed backups are detected early. Adjustments are made before problems grow. Monitoring also helps plan future capacity needs. Data systems remain responsive and reliable. Proactive care supports long-term efficiency and stability.
Supporting Compliance and Data Retention
Many industries face data regulations. Managed IT services help businesses meet compliance requirements. Data retention policies define how long information is stored. Sensitive data is handled according to legal standards. Audit trails track access and changes. Documentation supports regulatory reviews. This structured approach reduces the risk of penalties. Compliance becomes part of daily operations rather than a separate burden.
Building Resilience Through Continuous Improvement
Data environments evolve over time. Managed IT services review strategies regularly. Backup methods and storage solutions are updated as technology changes. Lessons from incidents guide improvements. Training and documentation stay current. This ongoing refinement shows utmost commitment to resilience. Businesses benefit from systems that adapt and remain dependable under pressure.
Managed IT services bring clarity and protection to data management and backup. They combine automation, security, and planning into one approach. Businesses gain reliable access to information and confidence in recovery. Centralized systems reduce complexity. Secure backups guard against loss. With expert support, data becomes an asset rather than a risk. Managed IT services help ensure information remains …






















 This classic piece of equipment has been a staple in the industry for decades, capturing some of the most memorable moments in cinematic history. With its impressive image quality and versatility, it’s no wonder that filmmakers continue to choose this tried-and-true workhorse. The 35mm film camera works by exposing photographic film to light through a series of intricate mechanisms. As each frame is exposed, it creates a tangible physical negative that can be developed and edited. This analog process delivers a unique aesthetic charm that digital cameras often struggle to replicate.
This classic piece of equipment has been a staple in the industry for decades, capturing some of the most memorable moments in cinematic history. With its impressive image quality and versatility, it’s no wonder that filmmakers continue to choose this tried-and-true workhorse. The 35mm film camera works by exposing photographic film to light through a series of intricate mechanisms. As each frame is exposed, it creates a tangible physical negative that can be developed and edited. This analog process delivers a unique aesthetic charm that digital cameras often struggle to replicate. These state-of-the-art devices basically make use of cutting-edge technology to deliver high-resolution images with incredible clarity and detail. Thanks to their ability to shoot in various formats, such as RAW or ProRes, they allow for greater flexibility during post-production. Filmmakers can manipulate the footage to achieve their desired look and feel, whether it’s adding special effects or adjusting color grading. Moreover, these cameras offer exceptional low-light performance, ensuring that even dimly lit scenes are captured without compromising quality. This feature greatly enhances a cinematographer’s creativity by expanding shooting possibilities in challenging environments. Additionally, digital cinema cameras often come equipped with advanced features like built-in image stabilization and high-speed frame rates.
These state-of-the-art devices basically make use of cutting-edge technology to deliver high-resolution images with incredible clarity and detail. Thanks to their ability to shoot in various formats, such as RAW or ProRes, they allow for greater flexibility during post-production. Filmmakers can manipulate the footage to achieve their desired look and feel, whether it’s adding special effects or adjusting color grading. Moreover, these cameras offer exceptional low-light performance, ensuring that even dimly lit scenes are captured without compromising quality. This feature greatly enhances a cinematographer’s creativity by expanding shooting possibilities in challenging environments. Additionally, digital cinema cameras often come equipped with advanced features like built-in image stabilization and high-speed frame rates. These compact and maneuverable devices allow cinematographers to achieve angles and perspectives that were once only possible with expensive helicopter rigs or cranes. One of the key advantages of using drone cameras is their ability to fly at different altitudes, providing a unique bird’s-eye view of a scene. This opens up endless creative possibilities for filmmakers to showcase sweeping landscapes or create dynamic chase sequences. With advancements in technology, drone cameras now offer high-resolution image quality, allowing for crystal-clear footage even when capturing fast-paced action scenes. They are equipped with stabilizing features that help eliminate shaky footage, ensuring smooth and professional-looking shots.
These compact and maneuverable devices allow cinematographers to achieve angles and perspectives that were once only possible with expensive helicopter rigs or cranes. One of the key advantages of using drone cameras is their ability to fly at different altitudes, providing a unique bird’s-eye view of a scene. This opens up endless creative possibilities for filmmakers to showcase sweeping landscapes or create dynamic chase sequences. With advancements in technology, drone cameras now offer high-resolution image quality, allowing for crystal-clear footage even when capturing fast-paced action scenes. They are equipped with stabilizing features that help eliminate shaky footage, ensuring smooth and professional-looking shots.
 Businesses need to be able to manage data to make informed decisions and stay competitive effectively. Investing in a good customer relationship management (CRM) system can help you keep track of customer information, sales history, and other important data points. You’ll also want to look into software for managing finances and inventory.
Businesses need to be able to manage data to make informed decisions and stay competitive effectively. Investing in a good customer relationship management (CRM) system can help you keep track of customer information, sales history, and other important data points. You’ll also want to look into software for managing finances and inventory.
 Having mobile access to your data is becoming increasingly crucial for businesses in today’s world. Investing in an excellent mobile platform will allow you to access and work on files anytime. It can improve collaboration and productivity and give customers easy access to your products and services.
Having mobile access to your data is becoming increasingly crucial for businesses in today’s world. Investing in an excellent mobile platform will allow you to access and work on files anytime. It can improve collaboration and productivity and give customers easy access to your products and services.
 One of the biggest mistakes businesses make when creating an app is focusing too much on features rather than the user experience. It’s important to remember that people use apps because they’re convenient and easy to use. If your app is difficult to navigate or isn’t intuitive, people will quickly get frustrated and stop using it.
One of the biggest mistakes businesses make when creating an app is focusing too much on features rather than the user experience. It’s important to remember that people use apps because they’re convenient and easy to use. If your app is difficult to navigate or isn’t intuitive, people will quickly get frustrated and stop using it.
 The first and most obvious benefit of using node as a Service is that it allows you to manage your blockchain efficiently and effectively. If you’re running a node yourself, you’ll need to keep up with the latest software updates, monitor the performance of your node, and ensure that it remains online and accessible. It can be time-consuming and difficult, especially if you’re not a technical expert.
The first and most obvious benefit of using node as a Service is that it allows you to manage your blockchain efficiently and effectively. If you’re running a node yourself, you’ll need to keep up with the latest software updates, monitor the performance of your node, and ensure that it remains online and accessible. It can be time-consuming and difficult, especially if you’re not a technical expert. A Node is a Service provider that can pre-configure superficial nodes across many chains and networks. You don’t need to worry about setting up and configuring your nodes yourself. All you need to do is provide the required information and funds, and the node will be set up and maintained by the service provider.
A Node is a Service provider that can pre-configure superficial nodes across many chains and networks. You don’t need to worry about setting up and configuring your nodes yourself. All you need to do is provide the required information and funds, and the node will be set up and maintained by the service provider.
 A spy app is a smartphone application that can be used to monitor another person’s mobile phone activity. This includes text messages, emails, calls, and anything else sent using the device. There are many reasons why someone might want to use a spy app on their child or spouse. They could be worried about their child being bullied at school or if their spouse is cheating on them. To use these apps, install the app from Google Play Store and follow its instructions to access your logs.
A spy app is a smartphone application that can be used to monitor another person’s mobile phone activity. This includes text messages, emails, calls, and anything else sent using the device. There are many reasons why someone might want to use a spy app on their child or spouse. They could be worried about their child being bullied at school or if their spouse is cheating on them. To use these apps, install the app from Google Play Store and follow its instructions to access your logs. WhatsApp logs are files that contain information about your conversations, such as the time and date of each message. You can use these logs to spy on someone’s WhatsApp messages because they provide a way to see all of their activity in one place. The easiest way to access is by using an app like WhatsDog or Monitor for WhatsApp. Both apps are free and work on Android devices. They allow you to download a copy of your WhatsApp conversations and view them in an easy-to-read format.
WhatsApp logs are files that contain information about your conversations, such as the time and date of each message. You can use these logs to spy on someone’s WhatsApp messages because they provide a way to see all of their activity in one place. The easiest way to access is by using an app like WhatsDog or Monitor for WhatsApp. Both apps are free and work on Android devices. They allow you to download a copy of your WhatsApp conversations and view them in an easy-to-read format.
 One of the essential features of a VPN is its strong encryption. It means that your data will be securely encrypted, making it difficult for anyone to spy on or track your activities. A reliable VPN provider will have robust security features, including military-grade encryption. It will also have a strict no-logs policy, meaning that your data will never be stored or tracked.
One of the essential features of a VPN is its strong encryption. It means that your data will be securely encrypted, making it difficult for anyone to spy on or track your activities. A reliable VPN provider will have robust security features, including military-grade encryption. It will also have a strict no-logs policy, meaning that your data will never be stored or tracked. Another essential factor in a reliable VPN provider is the privacy policy. A good VPN should have an airtight privacy policy so that your data remains secure and private while you are using their servers. Furthermore, since no one can see what sites or services you visit, it also means that even your ISP won’t track your activities.
Another essential factor in a reliable VPN provider is the privacy policy. A good VPN should have an airtight privacy policy so that your data remains secure and private while you are using their servers. Furthermore, since no one can see what sites or services you visit, it also means that even your ISP won’t track your activities.
 If you are running a small business, you do not have adequate resources to check your systems for security vulnerabilities. Robust firms provide you access to security experts. These experts can discover and fix weak areas in your applications and networks. When choosing an IT support firm, make sure you consider various professional certifications. Also, you should consider experience.
If you are running a small business, you do not have adequate resources to check your systems for security vulnerabilities. Robust firms provide you access to security experts. These experts can discover and fix weak areas in your applications and networks. When choosing an IT support firm, make sure you consider various professional certifications. Also, you should consider experience. The right IT support firm does not allow your tickets to go unanswered. Instead, it should always communicate the status of the open tickets and work to resolve them. There is a need to have a service level agreement. This helps mitigate arising issues because you have documented all the services you need. If your IT support company fails to meet the agreed targets, you should consider switching providers.
The right IT support firm does not allow your tickets to go unanswered. Instead, it should always communicate the status of the open tickets and work to resolve them. There is a need to have a service level agreement. This helps mitigate arising issues because you have documented all the services you need. If your IT support company fails to meet the agreed targets, you should consider switching providers.


 Slow operating servers and unresponsive datastores could cost you days or weeks of operation. It will, in turn, lead to poor customer service and low productivity.
Slow operating servers and unresponsive datastores could cost you days or weeks of operation. It will, in turn, lead to poor customer service and low productivity.